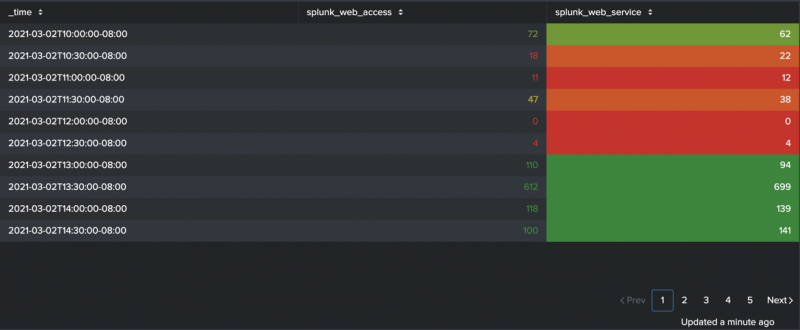
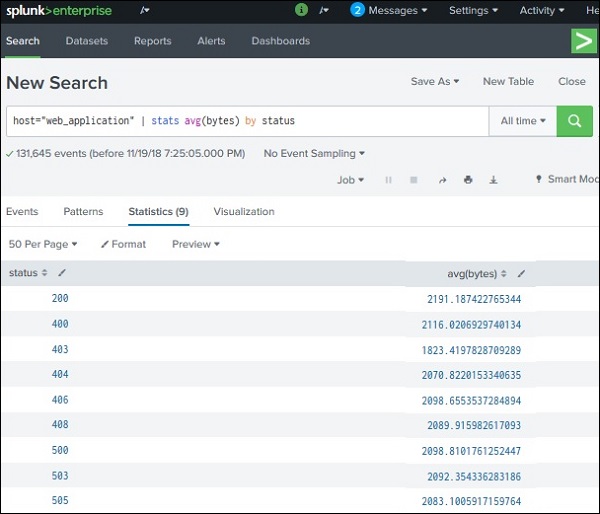
The table command is similar to the fields command in that it lets you specify the fields you want to keep in your results. Given the following query the results will contain exactly one row with a value for the field count.
I find them by using rex and then display them in a table.
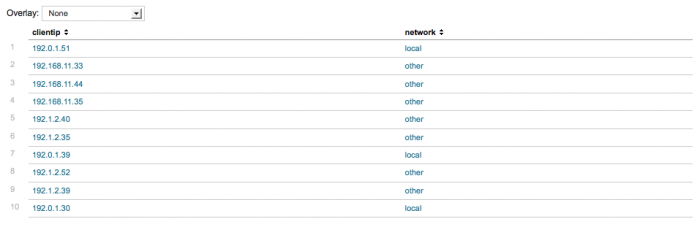
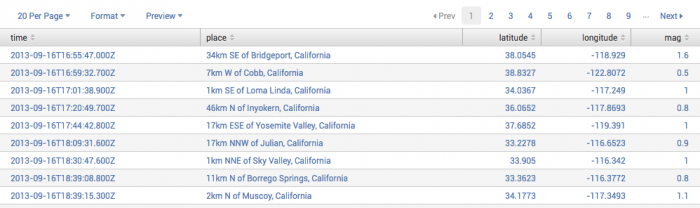
Table unique values splunk. Rare url Remove duplicates of results with the same host value and return the total count of the remaining results. With the exception of a scatter plot to show trends in the relationships between discrete values of your data you should not use the table command for charts. In the above query _internal is the index and splunkd_ui_access is the sourcetype.
Sourcetypeaccess_combined status404 dedup user table user. When Splunk reads the uploaded machine data it interprets the data and divides it into many fields which represent a single logical fact about the entire data record. Help creating a table that shows unique events from last 24hrs that have not occurred within the last 30days splunk-enterprise table subsearch unique featured edited Dec 10 19 by JAvnaim 22.
The simplest stats function is count. A Splunk lookup table has a few requirements as follows A table must contain a minimum of two columns Each of the columns in the table can have duplicate values You should use plain ASCII text and not non UTF 8 characters Now from Splunk Web we can click on Settings and then select Lookups From the Lookups page we can select Lookup Feb 26 2020 To get unique number of rows from the 39 orders 39 table. Use stats sum value_field_name by group_field_name.
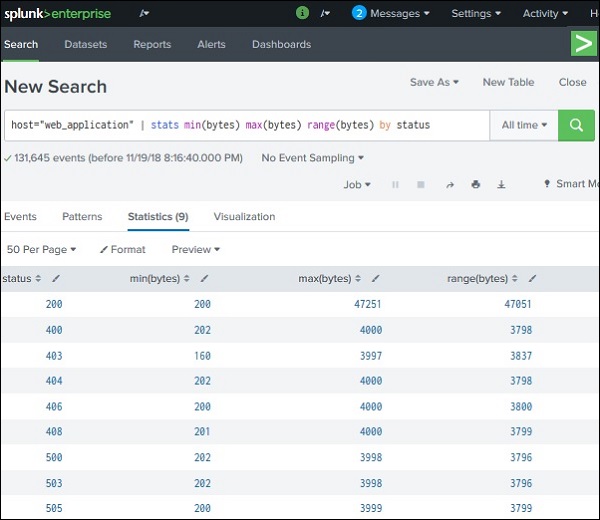
Now we use untable command in. The Splunk stats command calculates aggregate statistics over the set outcomes such as average count and sum. Customerjohn doe order_value100.
Learn more about the commands used in these examples by referring to the search. It is analogous to the grouping of SQL. In this section we are going to learn about the Splunk Stats strcat and table command.
AA_d BB_d table id. Inputlookup yourlookuptableNamecsv dedup primarykeyfieldprimarykeyfieldsSeparatedByComma. The snowtbl_endpointconfspec file in the README folder gives a description of the keyvalue.
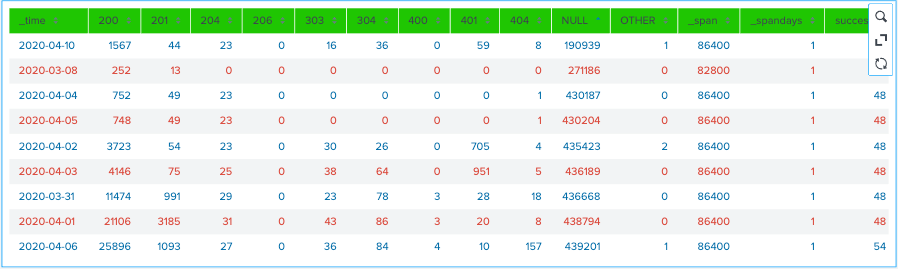
Top command will give the count and percentage of method field values in descending order in count and percent field respectively. Usage OF Stats Function first last earliest latest In Splunk. This command is used to split the values of a field that appear like a single value into multiple values within an event based on the delimiter.
Splunk - Field Searching. Outlier Return the least common values of the url eld. Remove all outlying numerical values.
As in the Matching IPs recipe you can specify a match_type for a lookup in the transformsconf config file. Assuming your source type is called access_combined and you have a status and user field defined either by Splunk automatically or explicitly by you via Field Extraction your search might look like this. For example a single record of information may contain server name timestamp of the event type of the event being logged whether login attempt or a.
The following steps are an overview of creating a custom ServiceNow Alert Action for the SNOW Table for Splunk app. Splunk stats strcat and table command. Per Splunks documentationrecommendations all changes should be in the local folder and restart of Splunk is required to enable changes.
But as the name field values Shilpa and Palash have unique age field values ie. You can also know about. Add a stanza with an unique name to the snowtbl_endpointconf file using one of the existing stanzas as a guide.
You can use dedup command to remove deplicates. Example Sum the total order value for each different customer. Some of those key IDs are duplicates.
Customerjohn doe order_value20. Search CheatSheet Here are some examples illustrating some useful things you can do with the search language. By including wildcard characters in your lookup table values you can direct Splunk to match on wildcards.
OR you could try this one as well which uses the distinct count operation. Many of the functions available in stats mimic similar functions in SQL or Excel but there are many functions unique to Splunk. 29 and 19 respectively they are still single value row.
NsmyApplication trying to insert document with keyId rex fieldmessage. A delimiter specifies the boundary between characters. Customermary white order_value25.
Mylookup match_type WILDCARDurl Learn more about Splunk in this insightful blog now. The values in the groceries field have been split within the same event based on the comma delimiter. Use table command when you want to retain data in tabular format.
Stats dchost Return the average for each hour of any unique eld that ends with the string lay for. Group by sumPermalink. We have also explained the differences among them.
I only want to show unique key IDs in the table. Just identify the fields which can be used to uniquely identify a student as studentID OR firstname-lastname combination OR something and use those fields in dedup.
Splunk Field Searching Tutorialspoint
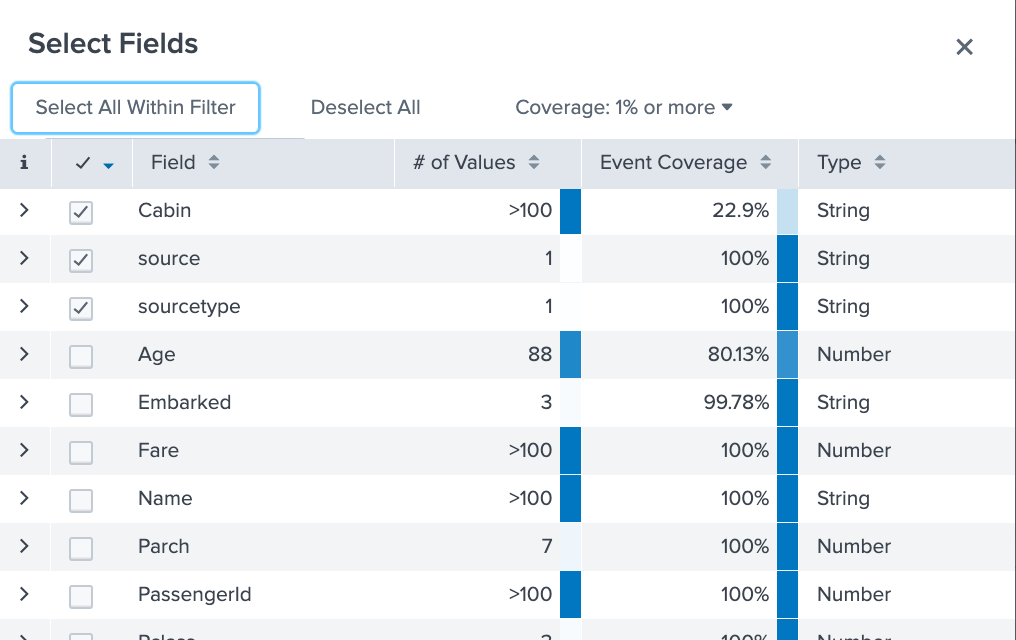
Splunk Field Search Splunk Tutorial Python Tricks
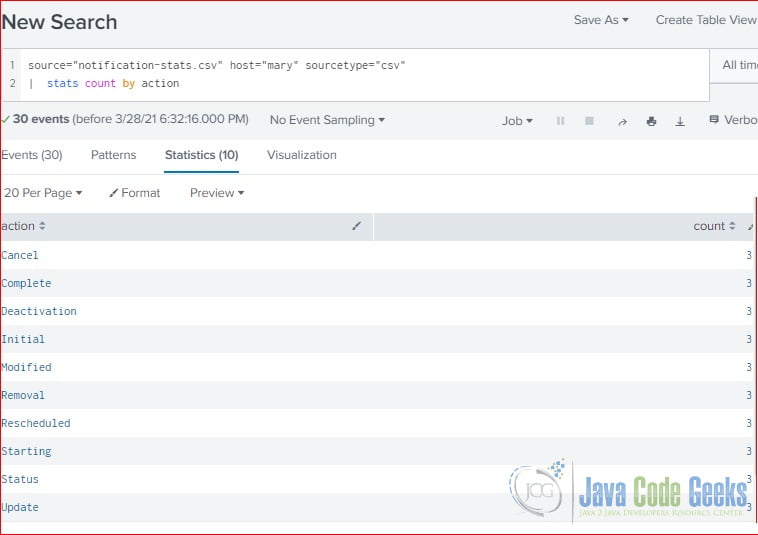
Splunk Stats Command Example Examples Java Code Geeks 2021

Splunk Extracting Values For Table Stack Overflow
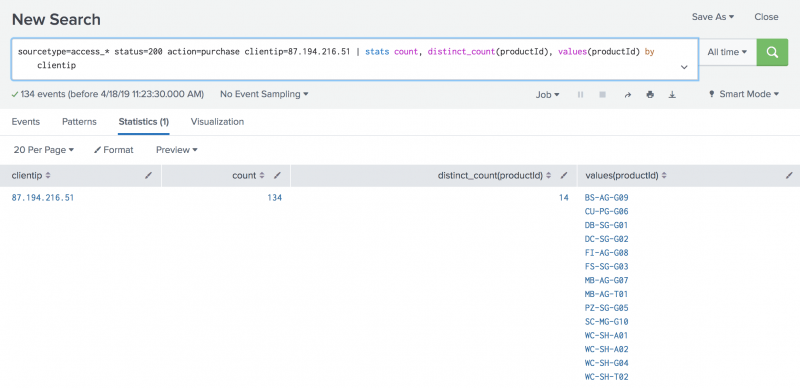
Use A Subsearch Splunk Documentation

Group Events By Multiple Fields In Splunk Stack Overflow

Usage Of Splunk Commands Mvcombine Welcome To Splunk On Big Data
Solved How To Create A Table Listing Users And Unique Val Splunk Community
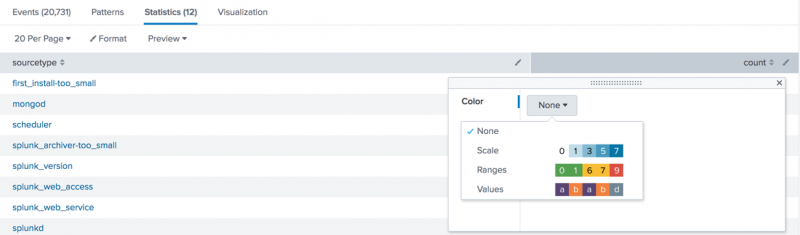
Format Table Visualizations Splunk Documentation

How To Find The Missing Values Of A Field By Comparing A Lookup File Welcome To Splunk On Big Data

Usage Of Eval In Splunk Welcome To Splunk On Big Data

Usage Of Splunk Commands Rex Welcome To Splunk On Big Data
Splunk Stats Command Tutorialspoint